BC Finance Leaders, Here’s what you need to know:
If you lead a financial institution in British Columbia, your regulatory obligations are about to change in ways that will fundamentally reshape how you approach cybersecurity. The Critical Cyber Systems Protection Act (CCSPA), contained in Bill C-8, represents the most significant federal cybersecurity legislation in Canadian history. For banking systems and clearing and settlement systems, compliance won’t be optional—it will be mandatory, enforceable, and backed by penalties severe enough to threaten institutional viability.
Understanding CCSPA’s Scope
CCSPA targets critical cyber systems across six federally regulated sectors:
- telecommunications,
- banking,
- clearing and settlement,
- energy, transportation,
- and nuclear systems.
If your institution operates banking systems overseen by the Office of the Superintendent of Financial Institutions (OSFI) or clearing and settlement systems under the Bank of Canada, you will be designated as a Designated Operator under the legislation.
This designation carries comprehensive compliance obligations that go far beyond general best practices. CCSPA establishes a mandatory regulatory framework requiring you to implement cybersecurity programs, report incidents within strict timelines, and comply with binding government directives.
The Core Obligations
Once your institution is designated under CCSPA, you face several immediate requirements that demand both technical capabilities and governance changes.
Cybersecurity Program Implementation
You have 90 days from designation to establish and implement a comprehensive cybersecurity program. This isn’t a checklist exercise. The program must include systematic risk identification and mitigation procedures, particularly for third-party vendor relationships. You need to conduct annual reviews and regular updates to ensure the program remains current with evolving threats.
The program must be documented, maintained, and stored within Canada. Regulators will have the authority to inspect your facilities, examine records and data, order internal audits of your cybersecurity practices, and issue binding compliance orders requiring corrective measures.
Incident Reporting Within 72 Hours
CCSPA requires you to report cybersecurity incidents to the Communications Security Establishment (CSE) within 72 hours. This timeline is absolute. You must provide technical data and information about affected critical cyber systems as part of your report.
For most financial institutions, meeting this deadline represents a significant operational challenge. You need the infrastructure to detect incidents in real time. You need classification procedures to determine what constitutes a reportable incident. You need established communication channels with regulators. You need documented response protocols that can be executed under pressure.
If your institution currently lacks 24/7 security monitoring, rapid incident assessment capabilities, or clear escalation procedures, you’re not prepared to meet CCSPA’s reporting requirements. The 72-hour clock starts ticking the moment an incident occurs, not when your IT team happens to discover it.
Supply Chain Risk Management
CCSPA recognizes that your cybersecurity is only as strong as your weakest vendor. You must identify and mitigate cybersecurity risks from third-party products and services. You must report material changes in supply chain arrangements or use of third-party products.
This means maintaining detailed vendor inventories that identify every service provider with access to your systems or data. It means conducting regular security assessments of these providers. It means ensuring your contracts include appropriate security requirements and audit rights. It means monitoring vendor compliance on an ongoing basis.
The regulatory framework makes clear that you remain accountable for vendor security. If a vendor incident compromises your systems, you still face the reporting requirements and potential penalties. You can’t outsource responsibility—only execution.
Governance and Accountability Requirements
CCSPA mandates that you notify regulators of material changes in ownership or control. You must comply with confidential cybersecurity directions issued by the government without disclosure. These directions can be issued without prior consultation, creating operational uncertainty around feasibility and cost implications.
Your board and senior management need to understand that cybersecurity is now explicitly a governance responsibility. Regulators expect executive oversight, adequate resource allocation, and regular reporting from cybersecurity teams to leadership.
Data Residency Obligations
CCSPA requires that detailed records of cybersecurity programs and incidents be stored within Canada. This aligns with broader regulatory trends. CIRO regulations already require that all cloud-hosted data reside in Canada, with encrypted data transit outside Canada limited to non-sensitive information that is fully encrypted.
If your institution currently uses international cloud providers or has systems with cross-border data flows, you need to conduct infrastructure assessments to identify where data resides. You need migration plans for systems that don’t meet residency requirements. You need contract modifications with service providers to ensure Canadian hosting. You need ongoing monitoring to prevent unauthorized data transfers.
The Penalties for Non-Compliance
CCSPA’s enforcement mechanisms include some of the most severe financial penalties in Canadian regulatory history. Organizations face up to $15 million per violation, per day. Individuals face up to $1 million per violation, per day. Directors and officers can be held personally liable for violations they were complicit in committing.
These aren’t theoretical maximums designed to intimidate. They’re real penalties that regulators can impose for failures to implement cybersecurity programs, report incidents within timelines, comply with government directives, or maintain adequate supply chain risk management.
Consider what this means in practical terms. If your institution experiences a cybersecurity incident and fails to report it within 72 hours, you face daily penalties that could reach $15 million. If your cybersecurity program is found inadequate during a regulatory inspection, the penalties accumulate daily until you achieve compliance. The financial exposure is extraordinary.
The Timeline You’re Working With
Bill C-8, containing CCSPA, was introduced in June 2025 and represents the government’s top cybersecurity priority. Legal and cybersecurity experts expect passage when Parliament resumes, likely between December 2025 and March 2026.
Once the legislation passes, you have 90 days from designation to establish your cybersecurity program. That timeline is shorter than it appears. Building robust compliance capabilities requires security infrastructure implementation, staff training and procedure development, vendor assessments and contract modifications, and testing and validation of incident response procedures.
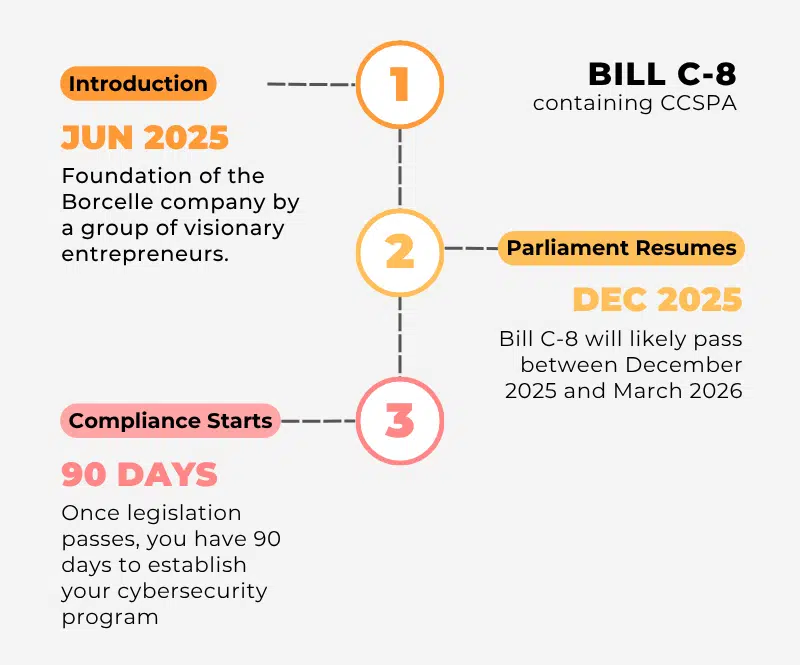
If you wait until CCSPA passes to begin compliance planning, you will be behind. Your competitors who start now will have tested, validated systems in place. You’ll be scrambling to meet minimum requirements while they focus on operational excellence.
Practical Steps to Prepare
Given the scope of CCSPA’s requirements and the compressed timeline for compliance, you should prioritize several actions now.
Assess Your Current State
Conduct a comprehensive gap assessment that maps your current cybersecurity controls against CCSPA’s anticipated requirements. Evaluate your incident detection and response capabilities against the 72-hour reporting requirement. Review all third-party vendor relationships for compliance gaps. Assess data residency for all systems processing sensitive information. Document your governance structures and board-level oversight mechanisms.
This assessment will reveal where you have compliance gaps and help you prioritize investments. Don’t assume your current security posture is adequate. CCSPA’s requirements go beyond general best practices to specific, auditable standards.
Build Incident Response Capabilities
Meeting the 72-hour reporting requirement is non-negotiable. You need to implement 24/7 security monitoring through either in-house security operations centers or managed security services. Establish clear incident classification criteria defining what constitutes a reportable incident. Create communication templates for regulatory notifications. Conduct regular incident response drills to test procedures under realistic conditions. Maintain detailed documentation of all incidents and responses.
These capabilities take time to build and refine. Running drills will reveal gaps in your procedures. Training staff on classification criteria requires repetition. Establishing reliable communication channels with CSE and your regulatory authority demands coordination.
Strengthen Vendor Management
Create a comprehensive inventory of all vendors with system access or data handling responsibilities. Conduct security assessments of critical vendors, including review of their SOC 2 reports or equivalent certifications. Ensure contracts include specific security requirements, audit rights, and incident notification obligations. Implement ongoing monitoring of vendor security posture. Establish clear procedures for vendor-related incident reporting.
Your vendor management program needs to evolve from periodic due diligence to continuous oversight. CCSPA requires you to report material changes in supply chain arrangements, which means you need real-time visibility into your vendor ecosystem.
Ensure Canadian Data Residency
Conduct a data flow analysis to understand where information is currently stored and processed. Work with cloud and service providers to ensure Canadian hosting. Modify contracts to include data residency guarantees and audit rights. Implement technical controls to prevent unauthorized data transfers. Establish regular audits to verify continued compliance.
Data residency isn’t just about where servers are physically located. It’s about ensuring data doesn’t inadvertently flow across borders during backups, disaster recovery procedures, or routine operations. You need both technical implementation and ongoing verification.
Establish Board-Level Governance
Your board needs to understand CCSPA’s requirements and the institution’s compliance status. Establish regular reporting mechanisms from cybersecurity teams to the board. Ensure adequate budget allocation for compliance initiatives. Document the board’s oversight role in cybersecurity risk management.
Regulators expect boards to be informed and engaged on cybersecurity matters. Directors can face personal liability for violations they’re complicit in, which creates a powerful incentive for meaningful oversight rather than perfunctory briefings.
The Role of Compliance-Focused Partners
For many mid-sized financial institutions, building all required capabilities in-house is neither practical nor cost-effective. Organizations with 50-250 employees lack the resources to maintain specialized security operations centers. They struggle to conduct continuous vulnerability assessments. Managing complex vendor due diligence programs proves challenging. Staying current with evolving regulatory requirements demands dedicated expertise. Responding to incidents within 72-hour timelines requires 24/7 capabilities.
This is where partnerships with compliance-focused managed service providers can help. These partnerships don’t replace your institutional responsibility. They act as a force multiplier that extends your capabilities. The key is selecting partners who understand CCSPA’s requirements and have the infrastructure to meet them.
When evaluating potential partners, look for SOC 2 Type II certification, comprehensive cybersecurity programs aligned with NIST frameworks, incident response capabilities designed to meet 72-hour reporting requirements, guaranteed Canadian data residency, proven vendor management programs, and deep knowledge of CCSPA, CIRO, and OSFI requirements.
Under CIRO rules, regulators and auditors must have the same access to service provider work product as they would if you performed activities internally. This means any partner you work with must maintain detailed records of all services provided. They must allow regulators to inspect systems and processes. They need to provide complete audit trails and support regulatory examinations.
The Bigger Picture
CCSPA represents a fundamental shift in how Canada regulates cybersecurity for critical infrastructure. The legislation recognizes that financial systems are vital to national security and public safety. Compromises to banking systems, clearing systems, or settlement systems could destabilize the Canadian economy.
This isn’t regulatory overreach. It’s a response to a genuine threat landscape. Cyberattacks targeting financial infrastructure are increasing in sophistication and frequency. Nation-state actors and criminal organizations view financial institutions as high-value targets. The costs of major incidents—measured in financial losses, operational disruption, and reputational damage—can threaten institutional viability.
CCSPA provides regulators with the tools to ensure financial institutions implement adequate protections. The mandatory cybersecurity programs, incident reporting requirements, supply chain oversight, and enforcement penalties create a regulatory floor that all designated operators must meet.
Moving Forward
The question for BC finance leaders isn’t whether CCSPA will pass—it’s whether your institution will be ready when it does. The regulatory framework is clear. The timeline is compressed. The penalties for non-compliance are severe enough to threaten your institution’s financial stability.
Institutions that begin compliance preparation now will be ready when CCSPA takes effect. They’ll have tested incident response procedures. They’ll have validated vendor management programs. They’ll have established governance processes that demonstrate board-level oversight. They’ll view the regulatory requirements as a foundation for operational excellence rather than a burden.
Those that delay will face a different reality. They’ll struggle to meet the 90-day deadline for cybersecurity program implementation. They’ll scramble to build incident response capabilities under regulatory scrutiny. They’ll face potential penalties while competitors who prepared in advance capture competitive advantages.
CCSPA is coming. The only variable is whether your institution will be prepared to meet its requirements or struggling to catch up when the legislation takes effect. The choice you make now will determine which scenario your institution faces in 2026.